Internet privacy with Next Generation IP tunneling protocol
You are interested in Internet privacy and You are using traditional old style IPsec or OpenVPN based tunneling protocols like IKEv1/IKEv2 or TLS which techologies coming from 90-ies. Big packet headers, lots of RTT-s, vast crypto libraries as openssl, weak encryption algorithms and security issues. Look at my talk and presentation in Cyberchess2019 conference (in Latvian) and appreciate next generation IP tunneling protocol WireGuard and compare it against old style VPNs. You could choose WireGuard clients as TunSafe for Windows 10, WARP from Cloudflare for Android and iOS with odd DoH/DoT! Good Luck!
Automatic SSL configuration generator
Configuring TLS is perhaps the most complicated and error-prone of all IT tasks, and this tries to make it as easy as possible. Mozilla recently developed and released SSL/TLS configuration generator
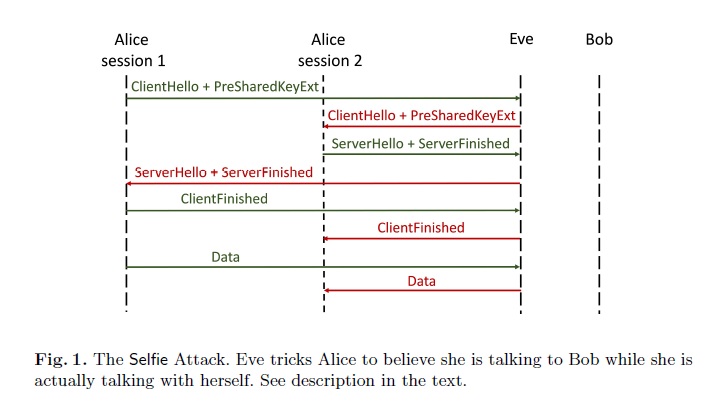
Selfie reflection attack against TLS 1.3 with PSK(Pre-Shared Key)
This attack affect psk_ke and psk_dhe_psk key exchange modes. This attack don't compromise communication channel's confidentiality and integrity.
If Alice share key with Bob, Eve could redirect TLS handshake packets back to Alice and Alice will send data himself such as: "If you have the file data.txt you can delete it. I hold a copy." If Alice, Bob and Carol share same PSK and Alice send data to the Bob, Eve could redirect TLS traffic to the Carol. In such situation Alice don't know actually that she speaks withs Carol. Selfie authors recommends using external PSK in conjuction with certificates or enforce user identification, which isn't easy task. To avoid need to using certificattes Selfie authors recommend:
"A PSK MUST NOT be shared between more than one client and one server."
Actually here is question, how wide external PSK are used. As PSK avoid using public key operation, this is useful in performance-constrained environments with limited CPU power. From practial viewpoint Selfie attack affects very small percentage of TLS commmunity (who use TLS-PSK nowadays!):
- CDN nodes acting as proxies
- P2P networks
- WiFi networks relying on one PSK
On the security of Smart-ID RSA digital signature scheme
I familiarized with Smart-ID technical overview and pay attention to the signature computation. From quick overview of detailed description of signature scheme, I infer usage of Distributed Multiprime RSA composite signature (client and Smart-ID server). Brilliant idea ... but with outdated and flawed signature implementation with RSASSA-PKCS1-v1_5 from RFC 3447. Inventors of Distributed Multiprime RSA strongly discourage usage of such weak signature implementation: "In practice RSA is never used without a secure padding scheme, such as PSS-RSA for signatures or OAEP-RSA for encryption. As show by Bleichenbacker's attack [Ble98] on the PCKS#1 v1.5 standard, provable security of RSA in combination with the padding scheme is very important." Developers of Smart-ID signature scheme didn't follow to inventor's recommendations and best practices. Other security researchers also indicate RSASSA-PKCS1-v1_5 to be vulnerable to the side-channel attacks.
Android 9 uses weak DH-1024 key exchange in IKEv1 main phase for IPsec tunnels
I' m using Android 9 and iOS 12.2 mobile devices. I have deployed strongSwan 5.7.2 IPsec gateway with following default encryption and key exchange (marked as red) settings:
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=3
ike=aes256-aes128-sha256-sha1-x25519-ecp256-modp2048-modp1024
esp=aes256-aes128-sha256-sha1
rekey=no
I have configured 2 L2TP/IPsec connections on Android 9 device: L2TP/IPsec-psk with shared secret and L2TP/IPsec-cert with client and server X.509 certificates. As L2TP authentication and authorization server I used Xelerance xl2tpd 1.3.10. I was very surprised when my sudo ipsec statusall returned dh-1024 key exchange in IKEv1 main mode!:
l2tp-psk[3]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
l2tp-cert[6]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
When I configured IPsec XAUTH (Cisco VPN) tunnel establishment with client and server X.509 certificates, I got the same key exchange result!:
ikev1-xauth[4]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
iOS 12.2 with same client configuration uses, contrary Android 9, dh-2048 key exchange:
ikev1-xauth[1]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
l2tp-psk[5]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
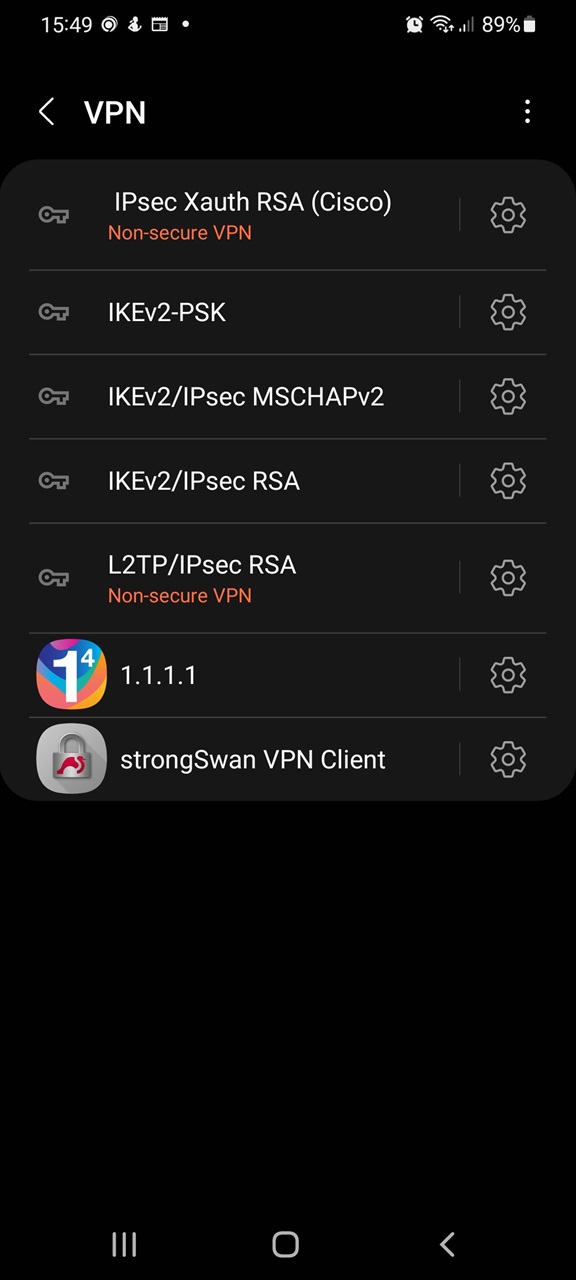
It is worth mentioned that dh-1024 bit key exchange is considered as weak, since 2015. As built-in Android 9 IPsec VPN client key exchange are weak, my recommendation is to install strongSwan VPN Client 2.1.0 with IKEv2 and X25519 or ECC P-256 key exchange:
ikev2-eap-md5[2]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519
In Andoid 9 IPsec key exchange case, I should say: "Old bones in new bag".
Ultimately Google after couple of years of 'SOS calls' heard my voice and added red warning in Android 12 about non-secure VPN connections with e.g. IPsec Xauth RSA and L2TP/IPsec RSA. Great! MODP_1024 key exchange problem still exist.